Online security has become a bit of a hot topic as of late. In the digital age, with digital citizens and digital identities, it makes sense that personal security would evolve with our technology.
Big data companies, like Facebook and Google, are gathering more and more information about individuals — such as their search histories, likes, and shares — every day, essentially reducing people’s online presence down to a portfolio of what users look at online. Sometimes, it’s hard to tell if corporations are on our side at all in terms of our online security, but there have always been people out there who definitely aren’t: hackers.
Now, hackers aren’t like the ones you see in Hollywood films. In actuality, Hollywood hacking has become something that gets poked fun at on the internet, with websites like hacktyper.com letting you mash random keyboard keys while outputting some sort of code on screen.
That being said, the hackers we think are always trying to steal our passwords and personal information aren’t really the ones we should be worried about.
What we usually think of as hackers are normally just conniving people who are trying to get you to give your accounts, money, information, etc. to them voluntarily through online scam techniques like phishing, ransomware, and catfishing (or “catphishing”). Phishing involves a fraudulent proposition, cat- phishing involves a fraudulent identity, and ransomware is an encryption virus.
Of the techniques, phishing is the most straightforward. The basic idea is that a phisher tricks someone into giving them information or money through fraudulent emails, messages, or phone calls. A commonly-employed trick phishers use is sending emails that look legitimate to scare users into giving them something like passwords or money to be relieved of the threat.
“There’s lots (of phishing scams) for banks,” MacEwan University computer science professor Cam McDonell says. “Lots for the Canada Revenue Agency . . . You’ll get a phone call saying, ‘Oh, there’s a correction to your taxes: you now owe $1,500. If you pay this immediately, there will be no further penalty. We advise you to handle this as quickly as possible.’ People are spooked by it.”
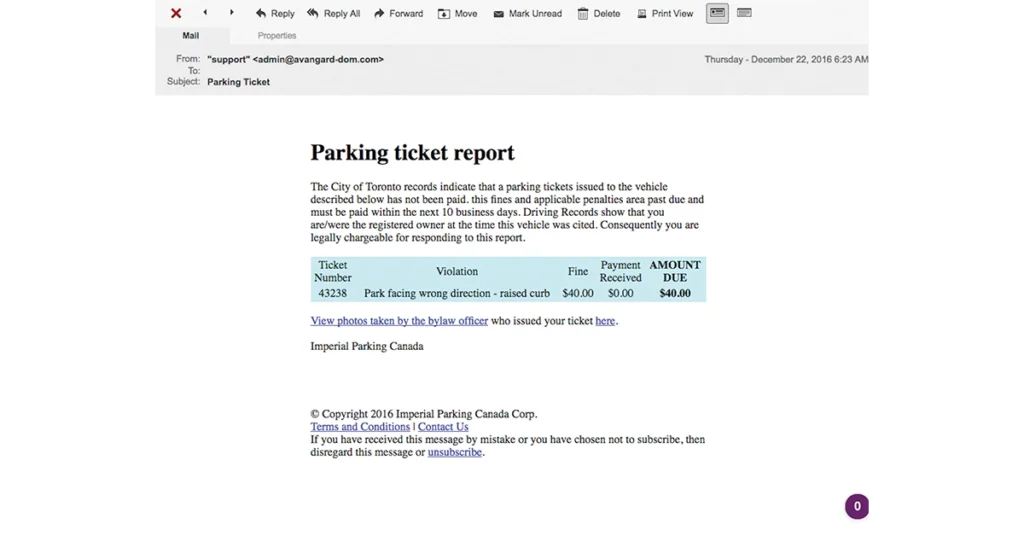
It’s a scam that works — and one that is bound to keep working as the world becomes increasingly reliant on technologies ranging from banking tools to social media.
There are phishing attacks that are based o of all kinds of elaborate lies, including fake parking tickets, phony security checks for passwords, and more. And they don’t always need to be large amounts of money to succeed.
“If the phishing attack is broad enough, if they just charge $50 and (the threat) will go away, well, trick 100,000 people and that is $5 million,” McDonell notes.
Although university students may usually be more aware of how technology works compared to the average person, they might not always be aware of their security.
“You’re not just gonna get an email saying, ‘Please submit your banking information here,’” McDonell says.
A lesson to be learned is perhaps that people need to begin thinking of their online presence and accounts more carefully due to hackers potentially accessing information we store on different platforms. From financial organizations to Facebook, the internet is beginning to contain more and more details about users’ offline identities. And due to the continual branching and consolidation of online platforms, one of our accounts can be linked to another, and another, creating a virtual paper trail of ourselves.
“An email address is your identity,” McDonell says.
‘The hackers we think are always trying to steal our passwords and personal information aren’t really the ones we should be worried about.
As users’ online paper trails grow, so do scammers’ resources.
Catphishers commit online identity theft to gather a network of information on individuals. And with an increased number of users engaging with social media, there is plenty of information available for catphishers to use against anyone with social media accounts.
Catphishing has had some light shed on it as of late, with shows like MTV’s Catfish: The TV Show highlighting the issues of sharing personal information on the internet and the dangers of online trust.
In brief, catphishing is tricking others into thinking you are someone else.
Catphishing has been especially prevalent on online dating sites and has been used for various nefarious purposes, ranging from money scamming to luring children, but it is mostly just used to mine information from users on the sites they target.
Catphishers often take what they can from public or unprotected social media profiles to start the process of impersonating someone. All the catphisher needs to find is a fake photo or name to bait someone into accepting a friend request, for example.
After a victim accepts the catphisher’s friend request, the catphisher will have all the information shared on the victim’s account and can easily take their identity next.
Like traditional identity theft, there is only so much a victim can do after they have been affected.
“The social media networks, like Facebook, are not dealing with it,” McDonell says.
Ransomware, another prevalent malware nowadays, is a virus that is affecting large organizations and individuals alike.
“The University of Calgary paid $20,000 to ransomware. The attackers got in and encrypted all of the emails. Faculty wouldn’t be able to use their email and would lose all their old emails,” McDonell says.
What if someone took the files on your PC, threw them in a safe, and politely asked you to pay cash for the key?
To take it even further, what if the malware gave the safe with your files to you, and told you to go to a scary alleyway so you could pay for the key to the safe?
If you replace the safe with complex algorithms and the key with an impossible string of numbers, you have ransomware. In addition, exchange cash for bitcoins and the scary alleyway for the darknet, an illicit “Wild West” version of the Internet.
Essentially, the whole scenario is like a tense hostage situation, complete with hostages and a ransom.
On account of all the nefarious online scams, MacEwan’s Technology Support department has tried to reduce the problem of online security with a campus-wide campaign to raise awareness, with posters mentioning keywords like phishing as a means of piquing student interest in the issue.
For tips on how to protect yourself from online threats like phishing, visit MacEwan’s Technology Support page online.
Cover photo supplied.





0 Comments